Here is a little guide on configuring your wireless network. If you have any questions feel free to ask.
- First off, personally I hate WLAN for its performance and overall suckyness. But as I understand people are using it, so here is a guide on how to properly configure and secure your wireless network to ensure the best performances possible.
I’ll first explain why wireless is generally worse than wired LAN connections.
First off, you can have a lot of issue’s with other devices interfering such as microwaves, TVs, portable devices, and of course other WLAN networks (I’ll come back to this later).
Second issue is that WLAN is half-duplex, meaning you can either send data, or receive it, but not at the same time. This means if your pc is sending a packet, your router has to wait till it received it, until it can start sending back to your PC.
The technique used to accomplish this is called Carrier Sense Multiple Access/Collision Detection, in short CSMA/CA. This technique checks if the channel is clear from any devices sending out data before it starts sending data on its own.
This is to ensure as much as possible that collisions don’t occur. When a collision occurs, both packages get damaged, and both parties will need to resend the data.
It does happen a lot that 2 devices check at the same time, find it clear, start sending, and still causing a collision. They will automatically put down a timer before it will try to resend.
As you can imagine, the more clients in a wireless network, or on the same channel, the more collisions you’ll get, and the slower your network becomes.
To make a long story short, WLAN is nice for browsing and such, but it’s not too good for gaming as you can see in the story above.
Now we can do some stuff to ensure you have the best possible connection if you chose to use WLAN anyhow.
To start off with, first make sure your receiving your signal at a proper strength. If your too far away from your access point, it will cause you to have a slow connection with a lot of packages not arriving at their destiny. If you have a fluctuating signal strength, you most likely have interference from other devices.
Now lets have a look at the channel setup.
You most likely have seen that you can configure your WLAN in a channel range somewhere from 1 to 13 depending on the country your in. One would think this would be 13 different channels to use, but its not what it seems. If you have 13 channels available, you only have 3 non-overlapping channels. All channels in between receive too much interference from the other channels next to it.
Commonly the only NON overlapping channels are 1, 6 and 13.
This picture illustrates channel overlapping on the 2.4Ghz 802.11 standard
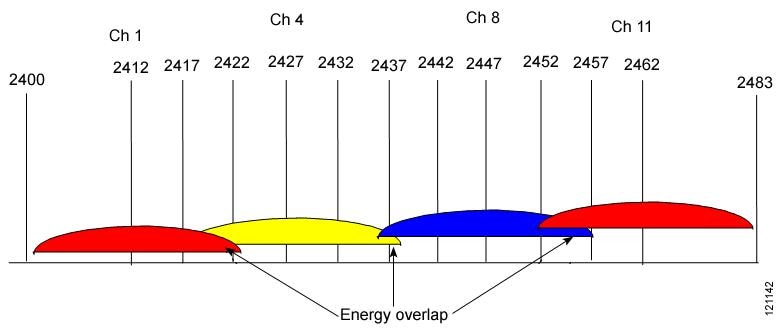
So what you need to ensure is that your WLAN is on a free, non-overlapping channel. If no non-overlapping channels are available, then pick the one which is most clear.
For example, if you have channels 1, 8 and 13 already in use by someone else, put your channel on 4.
Choosing the correct channel is one of the most important steps in configuring your WLAN. As you could read before, the more devices on a channel, the more collisions you get, and the slower the network performs.
Now you have selected a proper channel, its time to look at securing your network. I can be pretty straight forward in this.
- WEP security , its very weak and crack able under 2 minutes
- 802.1x EAP, weak security, crack able in a short time
- WPA, stronger security, but still quite easy to crack with the right attack/tools
- WPA2, most secure security protocol at the moment, use this when available
I won’t go into much details on the security, just use the highest on this list possible. If you don’t have WPA2 available, you could add an extra level of security by adding MAC address filtering. This isn’t very secure either, but the combination might scare people away because it takes more effort to crack. A MAC address is used to identify the network interface so it knows which packets to accept. A MAC address can easily be cloned, so only use MAC address filtering in combination with one of the listed security methods.